Enhancing Kubernetes Security through RBAC, Network Policies and Kubernetes Policies

Kubernetes, with its inherent flexibility and power, comes with a responsibility for robust security. We're not talking about just locking down your cluster, but about enabling a secure environment where developers can move fast without compromising on security. This guide will dive deep into best practices for managing Kubernetes, focusing on Role-Based Access Control (RBAC), Network Policies and Kubernetes Policies. We’ll explore common pitfalls and offer practical solutions
Challenge of Kubernetes Security
You're a developer in a fast-paced environment, constantly deploying new services and features. You need to be able to access the resources you need, but you also need to be confident that your actions are not putting the entire cluster at risk. This is the core challenge of Kubernetes security: how do you empower developers to move quickly while ensuring that your cluster remains secure?
The idea of granting broad permissions to everyone is often presented as a security risk, but in true DevOps Culture it’s rarely the actual practice in Kubernetes. Instead, the challenge lies in finding the right balance between security and developer productivity. This means implementing robust access control mechanisms, like RBAC, to ensure that developers have the necessary permissions to do their jobs without compromising the security of the entire cluster.
How RBAC Works in Kubernetes
Role-Based Access Control (RBAC) is a method for regulating access to computer or network resources based on the roles of individual users within an organization. In the context of Kubernetes, RBAC is used to manage who can access the Kubernetes API and what actions they can perform.
In Kubernetes, RBAC roles define a set of permissions, and role bindings associate these roles with users or groups. There are two types of roles:
- Roles: These are namespaced and define permissions within a specific namespace.
- ClusterRoles: These are cluster-wide and define permissions across the entire cluster.
Similarly, there are two types of role bindings:
- RoleBindings: These bind a role to users or groups within a specific namespace.
- ClusterRoleBindings: These bind a cluster role to users or groups cluster-wide.
Here’s a simplified example:
In this example, the pod-reader role allows read access to pods in the my-namespace namespace, and the read-pods RoleBinding assigns this role to the user Barry.
RBAC policies define roles, which are sets of permissions, and role bindings, which assign roles to users or groups. This approach allows for fine-grained control over access and actions within a Kubernetes cluster, ensuring that only authorized personnel can perform specific operations.
Common Pitfalls
- Over-privileged Users: Users are often given more permissions than necessary, increasing the risk of accidental or malicious actions.
- Lack of Auditing: Without proper auditing, it’s challenging to track who has access to what and identify potential security issues.
- Complex Role Definitions: Complex and overlapping role definitions can lead to confusion and misconfiguration.
Best Practices
- Define Clear Roles: Define clear and concise roles that reflect the actual needs of users. Avoid creating overly broad roles.
- Implement Least Privilege: Always grant the minimum required permissions. Regularly review and audit roles and bindings to ensure compliance with the principle of least privilege.
- Use Namespaces: Leverage namespaces to isolate resources and apply RBAC policies at the namespace level. This helps contain permissions and reduces the risk of widespread access.
- Regular Audits: Conduct regular audits of your RBAC policies. Use tools like kubectl to list roles and role bindings, and verify that they match your intended security posture
Let's look at an example. Imagine you have a development team working on a new microservice. You can create a role called "dev-team" that allows members of this team to create, update, and delete pods and deployments within a specific namespace. This ensures that they have the necessary permissions to work on their service, but they cannot access or modify other resources in the cluster.
Here's a snippet of how you might define this role in your Kubernetes YAML file:
This role grants the "dev-team" the ability to perform various actions on deployments and pods within the "my-namespace" namespace. You can create similar roles for other teams or individuals, tailoring permissions to their specific needs.
Network Policies
While RBAC controls access to Kubernetes resources, it doesn't address the flow of traffic between pods within your cluster. Network Policies act like firewalls, defining which pods can communicate with each other based on labels, namespaces, and other criteria.
Think of it this way: RBAC controls who can enter your house, while Network Policies control who can enter specific rooms within your house. By carefully configuring Network Policies, you can prevent unauthorized communication between pods, reducing the risk of attacks and data breaches.
Step-by-Step Guide:
- Label Pods for Identification: Start by labeling the pods that you want to include in your network policy. Labels are key-value pairs used for selecting pods. This step is crucial as network policies use these labels to identify the target pods.
- Define the Network Policy: Create a YAML file that defines your network policy. The policy specifies which pods can communicate with each other based on labels.
- Apply the Network Policy: Use kubectl to apply the network policy to your Kubernetes cluster.
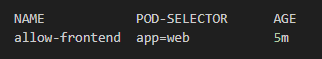
- Verify the Network Policy: Check that the network policy has been correctly applied by listing the network policies in the namespace.
You will get a similar output to this.
- Test the Network Policy: Verify the policy by testing the connectivity between the selected pods. Use tools like curl or wget to ensure that traffic is allowed according to the defined policy.
If the network policy is correctly configured, the above command should succeed, indicating that frontend-pod-1 can communicate with web-pod-1.
To test policy enforcement, try connecting from a pod without the allowed label. It should fail if the policy is correctly enforced.
Common Pitfalls
- Lack of Default Deny Policy: Many clusters lack a default deny policy, leaving them open to unintended communication between pods.
- Overly Permissive Rules: Network Policies are often too permissive, allowing more traffic than necessary and increasing the attack surface.
- Inconsistent Application: Policies are sometimes inconsistently applied across environments, leading to discrepancies between development, staging, and production.
Best Practices
- Implement a Default Deny Policy: Start by implementing a default deny policy. This ensures that no traffic is allowed unless explicitly permitted, reducing the attack surface
- Principle of Least Privilege: Apply the principle of least privilege to your Network Policies. Only allow the necessary communication between pods.
- Test Policies Thoroughly: Test your Network Policies in a staging environment before applying them to production. Use tools like kubectl to simulate traffic and verify the policies are working as intended.
Let's say you want to restrict communication between your database pods and any other pods in the cluster. You can create a Network Policy that allows only the web server pods to connect to the database pods. This prevents any other pod from accessing the database, even if it has the necessary RBAC permissions.
Here's a basic example of a Network Policy in YAML:
This policy allows pods with the label "app: webserver" to access the database pods within the "my-namespace" namespace. Other pods are blocked from accessing the database.
Kubernetes Policies
Now, let's talk about Kubernetes Policies. These are a powerful tool for enforcing cluster-wide rules and configurations. They provide a way to define constraints that apply to all resources within your cluster, ensuring consistency and security across the board.
Imagine you want to enforce a policy that all pods must run with a specific security context, such as a specific user ID or a set of capabilities. You can define a Kubernetes Policy to enforce this requirement, preventing the deployment of any pod that doesn't meet the criteria.
Here's a simplified example of a Kubernetes Policy in YAML:
Other security constraints can be defined here
This policy ensures that all pods run with a user ID between 1000 and 2000. You can define other security constraints, such as disabling privileged containers or limiting the capabilities of pods.
Complexity and Configuration Management in Kubernetes Security
While RBAC, Network Policies, and Kubernetes Policies are powerful tools, they can also be complex to configure and manage. Defining roles, policies, and constraints for every user, service account, and pod can be time-consuming and error-prone. It's easy to make mistakes that inadvertently restrict access or leave vulnerabilities open.
Furthermore, managing these configurations across multiple namespaces and clusters can become a logistical nightmare. You need a way to ensure consistency, track changes, and roll back configurations if necessary.
The Solution: Internal Developer Platforms for Streamlined Security
To tackle the complexities associated with RBAC, network policies, and Kubernetes policies, consider adopting an internal developer platform (IDP). An IDP can centralize and manage these security tools, providing a streamlined solution tailored for developers. This approach promotes developer self-service while ensuring that security measures are robust and compliant. The goal is to empower developers to deploy and manage applications independently.
An effective internal developer platform will offer:
- Pre-defined Templates and ValidationRules: These ensure that developers adhere to security best practices without needing deep expertise in Kubernetes security.
- Self-Service Tools: Developers can create and manage their roles and policies within the boundaries set by the platform.
- CI/CD Integration: Automate the deployment of security configurations alongside application deployments, ensuring that security is baked into the development process.
By providing these capabilities, an internal developer platform can significantly reduce the burden on your security team and enable faster, safer deployments. This ensures that while developers have the autonomy to manage their applications, their actions remain secure and compliant.
Beyond RBAC and Network Policies
RBAC and Network Policies are just two pieces of the Kubernetes security puzzle. You also need to consider other aspects, such as:
- Pod Security Policies: Define security constraints for pods, ensuring they meet specific security requirements.
- Admission Controllers: Enforce policies at the admission stage, preventing the deployment of insecure configurations.
- Image Scanning: Scan container images for vulnerabilities before deploying them to your cluster.
- Secrets Management: Securely store and manage sensitive data, such as API keys and database credentials.
- Logging and Monitoring: Track activity within your cluster and detect potential security threats.
Conclusion
By embracing RBAC, Network Policies, Kubernetes Policies, and other security best practices, you can build a secure and agile Kubernetes environment that empowers developers to move fast without compromising on security. The key is to strike a balance between control and agility, enabling developers to self-manage their security configurations while ensuring that your cluster remains protected. This approach not only enhances security but also fosters a culture of responsibility and collaboration, ultimately leading to a more secure and efficient development process.
FAQ
What is RBAC in Kubernetes?
RBAC (Role-Based Access Control) in Kubernetes manages user and service account permissions. It controls who can access what using Roles, RoleBindings, ClusterRoles, and ClusterRoleBindings to enforce security and least privilege. This ensures users and applications only have the permissions they need, reducing security risks.
How to check if RBAC is enabled in Kubernetes?
To check if RBAC is enabled in Kubernetes, run:
If RBAC is enabled, this command will return API versions like v1. You can also check the API server settings by running:
If the output includes "authorization-mode=RBAC", RBAC is active in your cluster.
Azure RBAC vs Kubernetes RBAC
Azure RBAC controls access at the Azure subscription, resource group, or resource level, managing who can create, delete, or modify resources like AKS clusters. Kubernetes RBAC, on the other hand, controls access within the Kubernetes cluster, managing what users and service accounts can do inside the cluster (e.g., creating pods, modifying deployments, or accessing secrets). Azure RBAC manages who can access the cluster, while Kubernetes RBAC manages what users can do inside the cluster.
What is the RBAC Writer role in Azure Kubernetes Service (AKS)
The RBAC Writer role in Azure Kubernetes Service (AKS) allows users to manage Kubernetes role-based access control (RBAC) settings without full administrative privileges. This means they can create, update, and delete RBAC roles and bindings within a Kubernetes cluster but cannot make broader cluster-wide changes. This role is useful for delegating access control responsibilities to security teams or DevOps engineers while maintaining cluster security.
How do I assign the Cluster Admin role in Azure Kubernetes Service (AKS)?
The Cluster Admin role in AKS grants full administrative access to a Kubernetes cluster. This role is typically assigned using Azure RBAC through the Azure Portal, CLI, or PowerShell. To assign a user the Cluster Admin role via the Azure CLI, use the following command:
While this role is useful for managing the entire cluster, it is recommended to follow the principle of least privilege and only assign Cluster Admin permissions when absolutely necessary. Overuse of this role increases security risks by giving users unrestricted control over Kubernetes resources. Instead, consider using more granular roles that provide only the necessary permissions.
Interesting Reads
The latest on DevOps and Platform
Engineering trends
Subscribe to our newsletter and stay on top of the latest developments

.avif)
.avif)
